STORMTM : Secure Tool for Risk Management
Governance, Risk & Compliance Tool

STORMTM
The STORM collaborative environment implements all the phases of STORM-RM methodology and offers them as friendly e-services. Specifically, the collaborative services offered to the STORM users (members of the security team, managers, administrators, end-users) by the STORM environment are:
-
- Cartography
-
- Data Identification and Data Mapping
-
- Identify and depict the ICT infrastructure
- Services identification
-
- ICT assets (software and hardware) identification
-
- Cartography
-
- Impact Assessment Service:
-
- Conduct Data Protection Impact Assessment (DPIA)
-
- Recognize the impacts (business, economical, technological, legal) of upcoming incidents on the operations of the ICT
-
- Impact Assessment Service:
-
- Threat Assessment Service:
-
- Identify threats
-
- Evaluate threats
-
- Threat Assessment Service:
-
- Vulnerability Assessment Service:n
-
- Identify Vulnerabilities
-
- Evaluate Vulnerabilities
-
- Vulnerability Assessment Service:n
-
- Risk Assessment service:
-
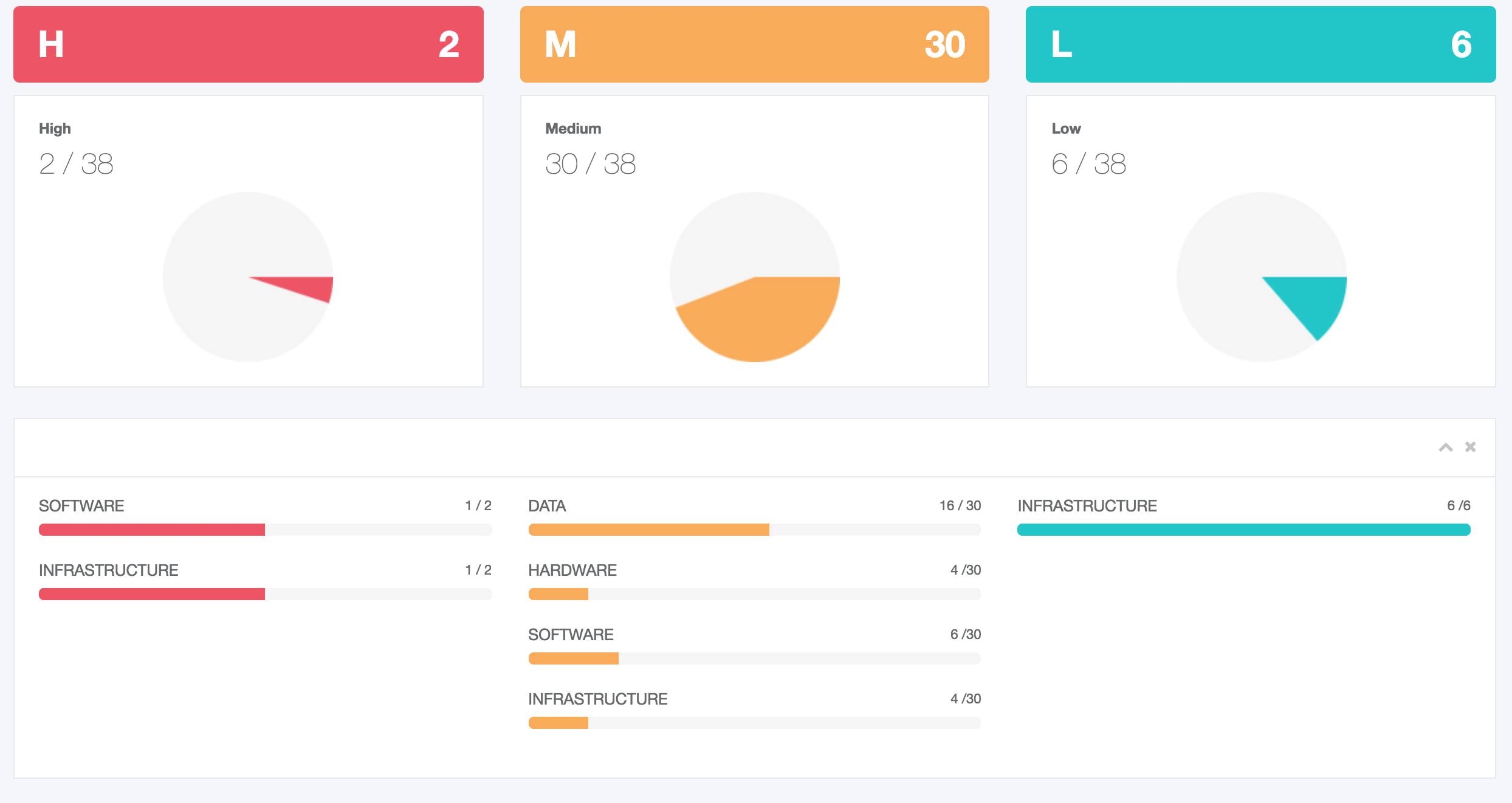
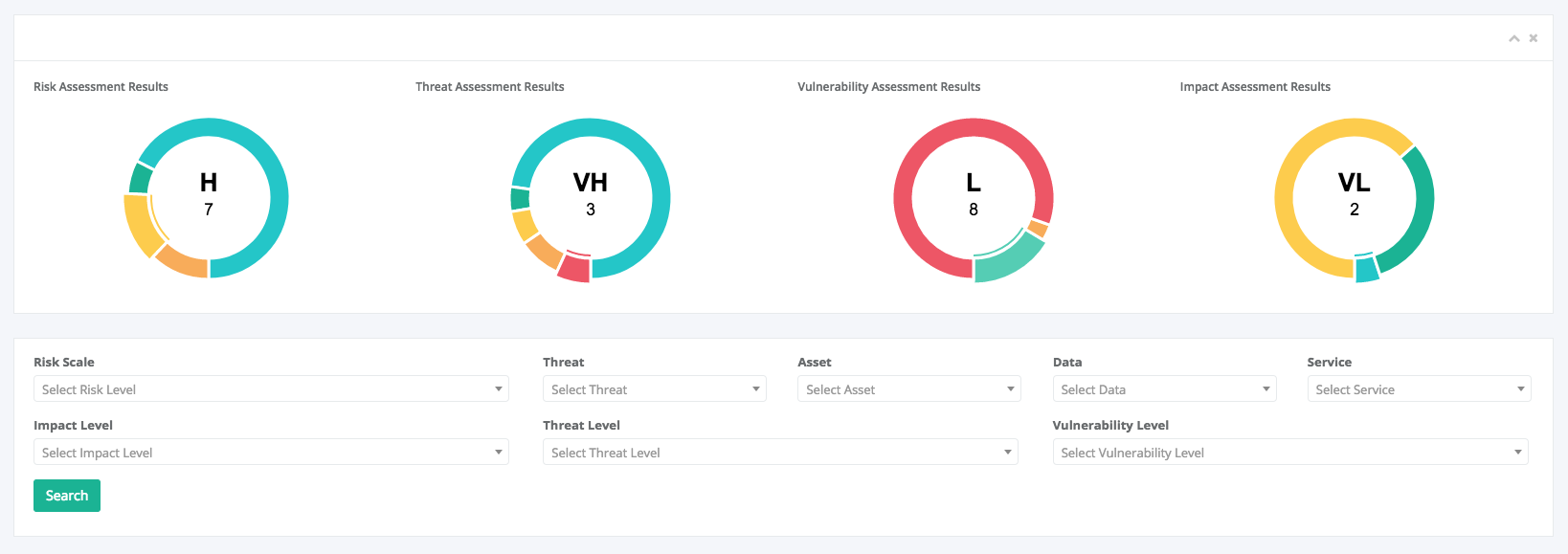
- Collaborative support towards identifying and evaluating the impact, threat and vulnerability of each ICT asset (i.e. software, hardware, data asset).
-
- Risk Assessment service:
-
- Risk Management service:
-
- Select the appropriate countermeasures according to the STORM-RM algorithm in order to protect ICT assets.
-
- Risk Management service:
-
- design, update and download as controlled PDF/DOCX file the Security Policies of their ICT (based on the security standard ISO 27001),
- design, update and download as controlled PDF/DOCX file all the necessary (mandatory or not) Security Procedures of their ICT systems (based on the security standard ISO 27001),
- implement Security Procedures via the Workflow Management Module. Define specific steps, roles and actions (i.e. approve, reject, implement) for each procedure,
- design, update and download as controlled PDF/DOCX file the Statement Of Applicability (SOA),
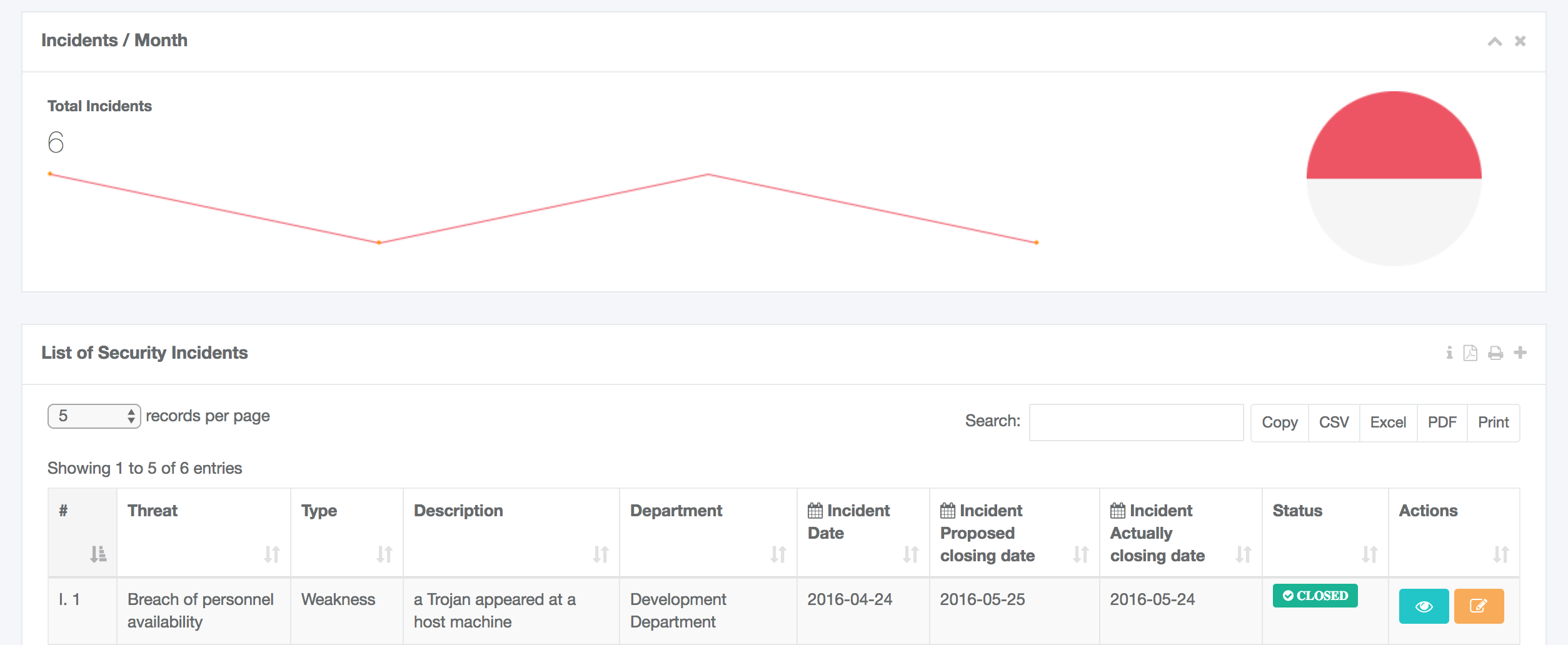
- report and manage Information Security Incidents. The STORM users are able to report any security incident with all the necessary information such as the date of the incident, the asset involved, the impact level of the specific incident, the corrective and preventive actions needed etc. Additionally, they are able to download as PDF/DOCX file the incident report form as well as the list with all the existing security incidents,
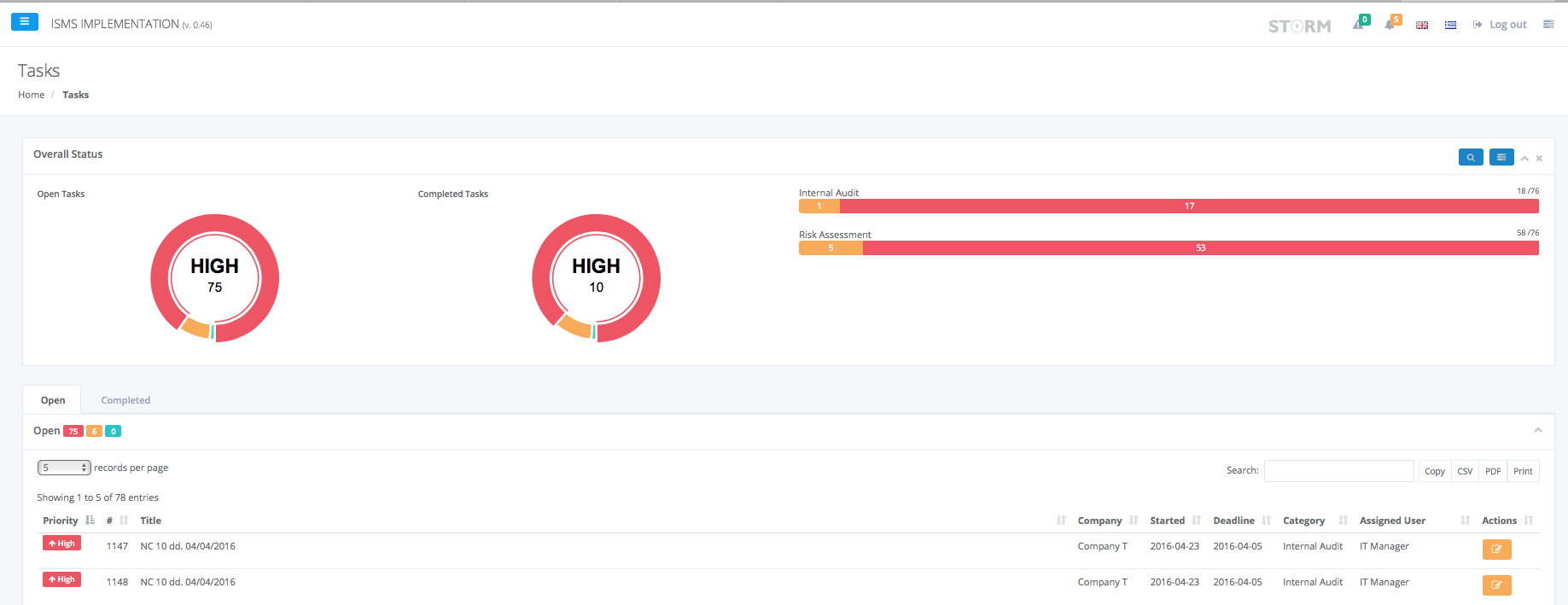
- report all possible Non-Conformities from internal audits and assign the corrective actions to the corresponding users via the Task Management Module,
- prepare the Internal Audit Report and download as controlled PDF/DOCX file,
- prepare the Information Security Management Reviews, identify the actions required in order to effectively review the Security Procedures, Policies and Risk Assessment Results. Additionally, all agreed actions at the Management Review Meetings will be assigned to the appropriate personnel in order to monitor their implementation status via the Task Management Module,
- Conduct 3rd Parties security assessments (i.e. GDPR assessments, ISO 27001 assessments).
-
- Forum
-
- Find immediate solutions to any everyday security problems
-
- Forum
-
- STORM Wiki and STORM Surveys
-
- Set up security awareness programs in order to ensure that all the organisation’s users are aware of the security policy, procedures and their responsibilities.
-
- STORM Wiki and STORM Surveys
STORM TM is an innovative, collaborative, cost effective and user friendly security consultancy environment that can be used by different type of organisations in order to collaboratively manage their information security. STORM can easily be parameterised in order to address the needs of different types of Information and Communication Technology (ICT) systems (i.e. critical infrastructures, SMEs).
STORM: A unified platform designed for compliance with industry specific cybersecurity requirements (e.g. ISO 27001, NIST CSF, GDPR, IMO, NERC CIP etc.)
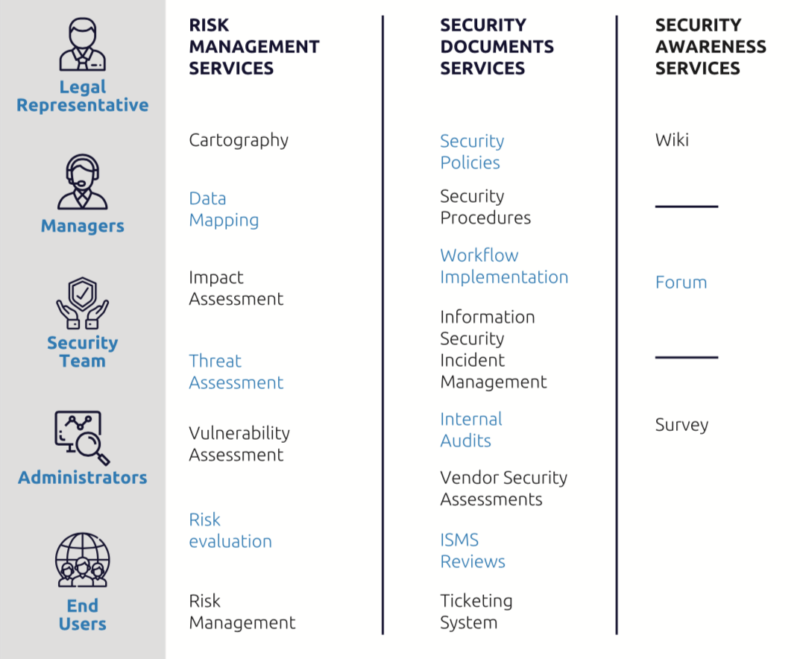
Risk Management Services
The main goal of this group of services is to conduct the Risk Assessment & Risk management. All the phases of STORM-RM methodology are implemented in an automated, self explanatory, user friendly mode by making use of interactive screens, online forms and help menus.
Identify your Information Assets via helpful online forms
Identify your Data Flows and prepare the Records of Processing Activities according to the GDPR requirements
Conduct Data Protection Impact Assessment (DPIA)
Conduct Business Impact Assessment (BIA)
- Select the appropriate mitigation actions via predefined security controls
- Download all reports in PDF / WORD / EXCEL format
Security Documents Services
This group of services is responsible for the creation and updating of all the security key documents.
- Security Policies & Procedures Creation
Implement Procedures via Workflow Mechanism
Information Security Incident Management
Conduct Management Reviews
Conduct Internal Audits against security standards (e.g. ISO 27001, ISO 22301, ISO 27017) & regulation (e.g. GDPR) requirements
Conduct Vendor Security Assessments against security standards (e.g. ISO 27001, ISO 22301, ISO 27017) & regulation (e.g. GDPR) requirements
Security Awareness Services (Wiki, Forum, Survey)
The goal of this group of services is to facilitate collaboration and exchange opinions and ideas on Information Security topics as well as to ensure the security awareness.
Via the Forum service, the users are able to find immediate solutions to any everyday security problems and they are able to be constantly informed of the security trends and issues by the use of Wiki.
Via the online Survey and STORM Wiki, you are able to set up security awareness programs in order to ensure that all the organisation’s users are aware of the security policies, procedures and their responsibilities.
Conduct Security Awareness programs
Enable users to participate to internal security forums
- Find immediately solutions to any security event
Banking & Insurance
Software Houses
Maritime Sector
Governmental Organisations
Cloud Providers
Energy Sector

IS IN OUR DNA.