WHAT WE DO.
ICT PROTECT is a firm specialising in Information Security Management, Cybersecurity and GRC Consulting services.
Our expertise lies in Risk Assessment, IT Audit, ISMS Development, GDPR compliance, Business Continuity, Security Assessments as well as Tailor-made Security Studies.
ICT PROTECT provides the professional security services you need in order to manage your information risks effectively. We offer a variety of compliance and assurance services and our mission is to help you protect your ICT systems.
ICT PROTECT has been certified with ISO 27001:2013, ISO 22301:2019, ISO 37001:2016, ISO 9001:2015, Cyber Essentials & Cyber Essentials Plus for its Consulting Services and STORM SaaS solution, to ensure that our services meet every time our very strict requirements and exceed our client’s specifications.


COMPLIANCE SERVICES
- GDPR Compliance
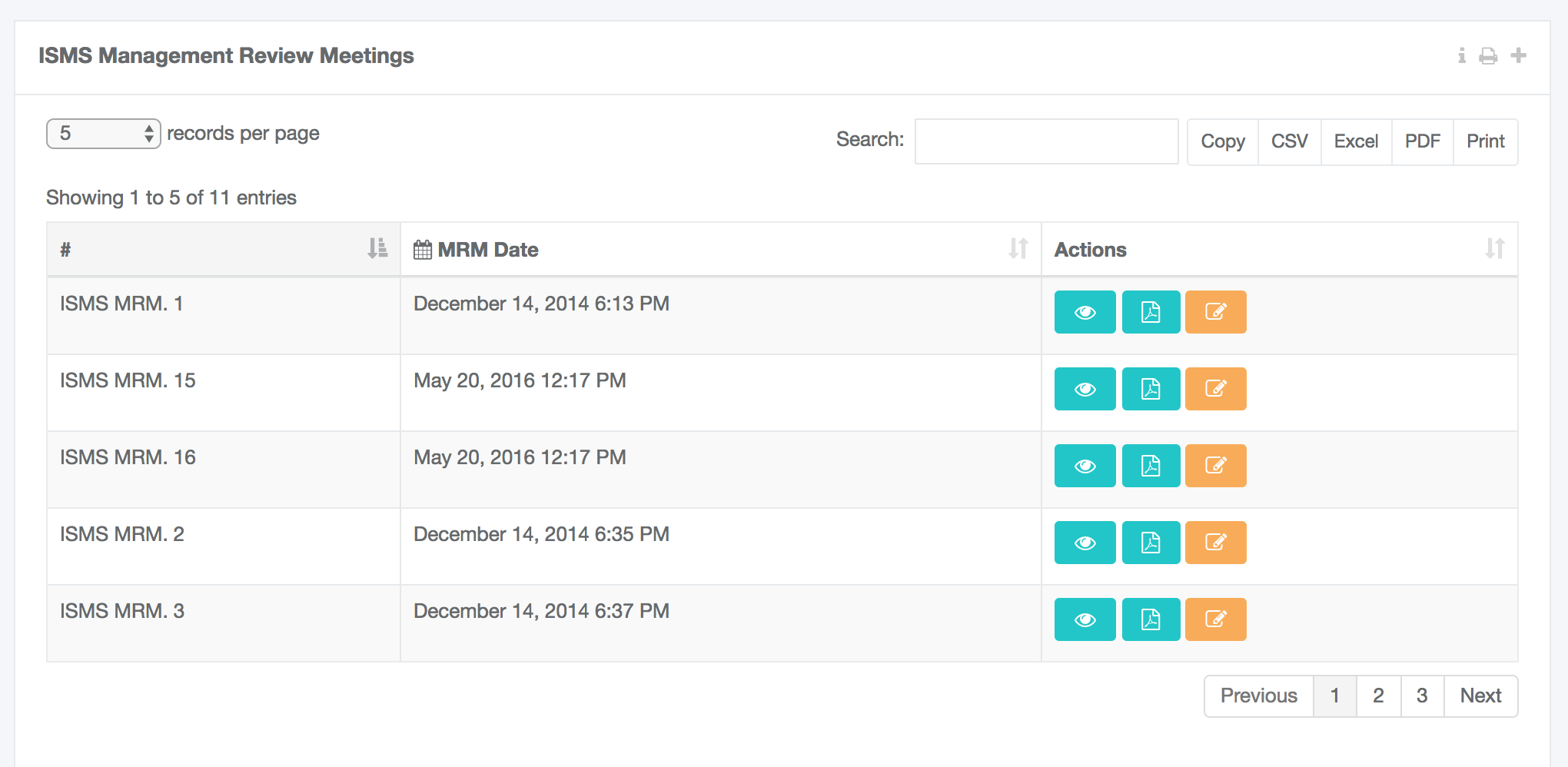
- Information Security Management System (ISO 27001) Implementation
- Business Continuity Management System (ISO 22301) Implementation
- Implement Security Controls for your Cloud Services (ISO 27017)
- Compliance Audit ( AICPA Trust Service Criteria – SOC 2 compliance, NERC CIP compliance audit, etc.)
SECURITY MANAGEMENT SERVICES
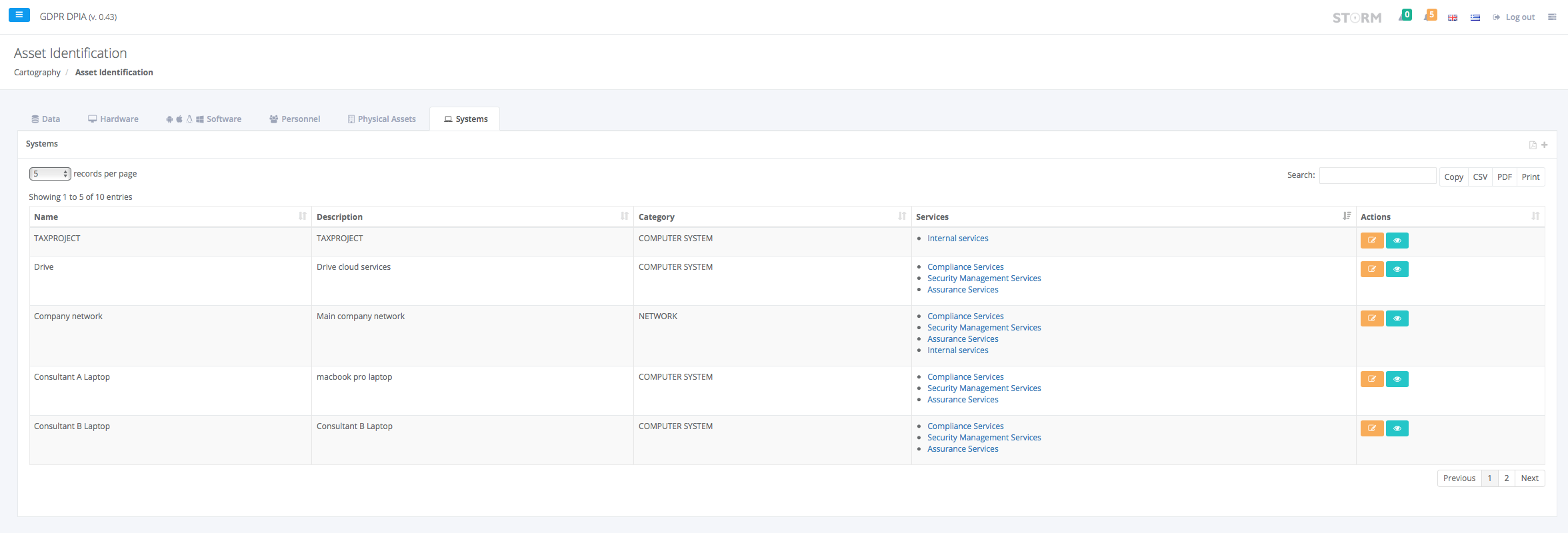
- Data Identification / Data Cartography
- Data Classification
- Security Plan / Security Roadmap
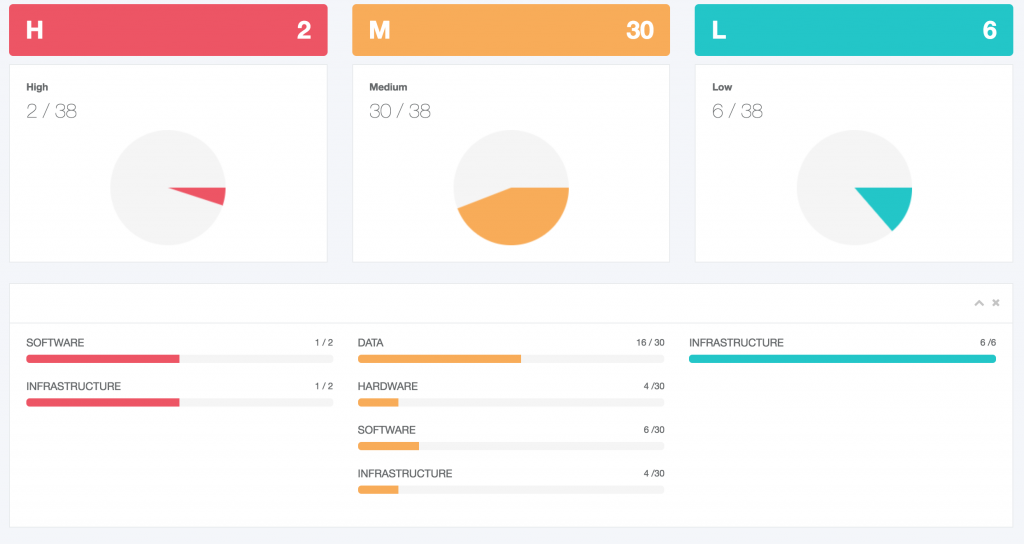
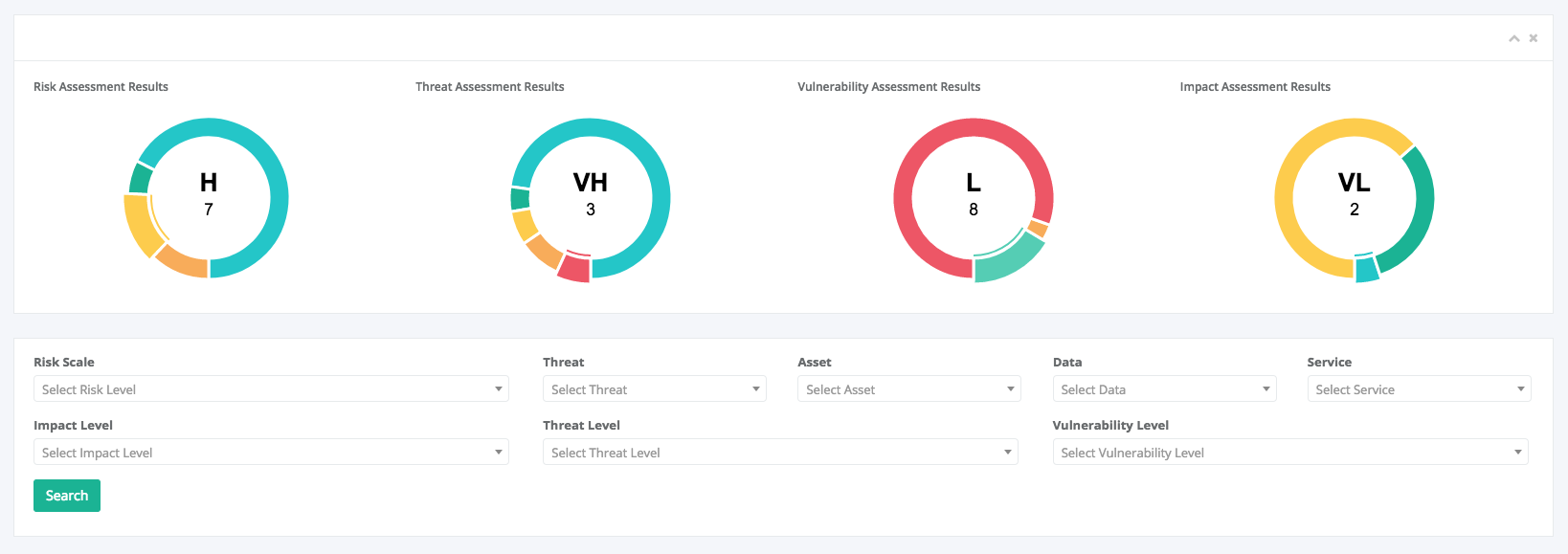
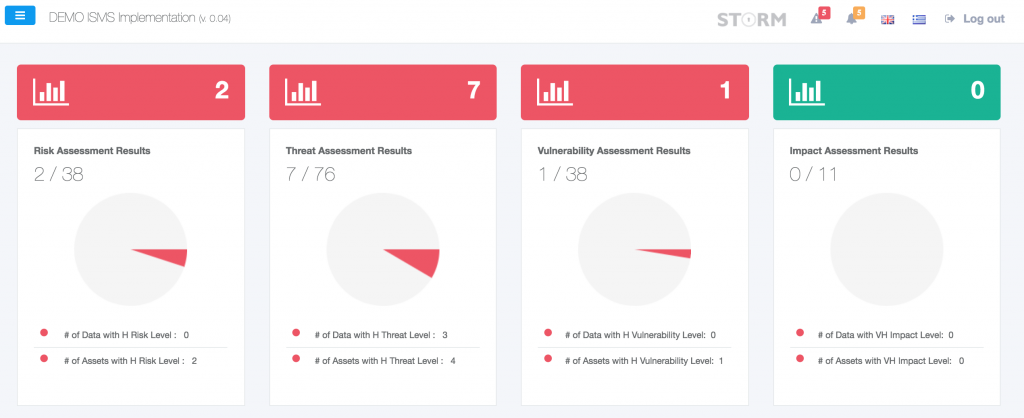
- Risk Assessment
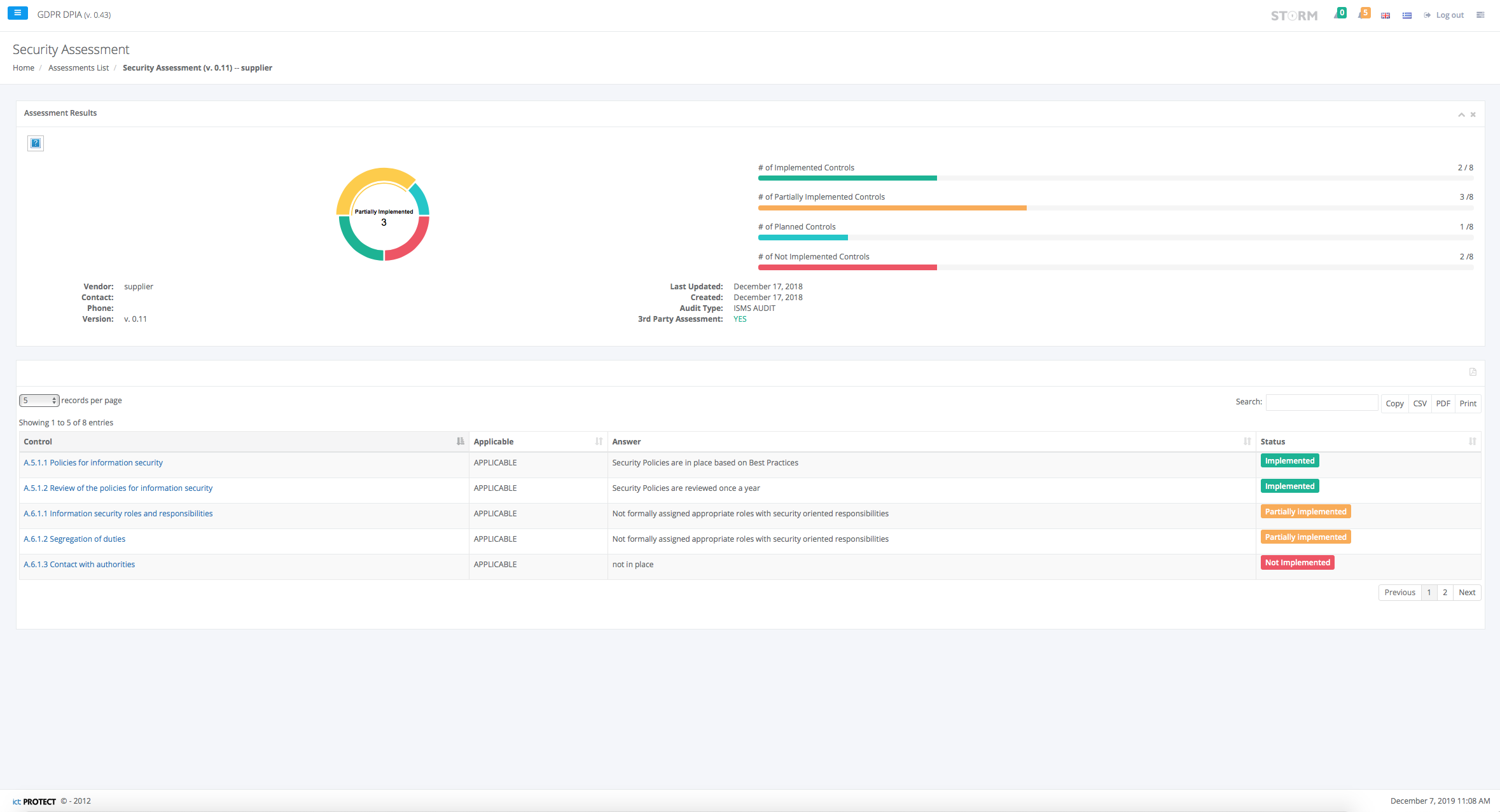
- IT Audit
ASSURANCE SERVICES
- Application Threat Modelling
- Web App Penetration Test
- Infrastructure Security Assessment
- Web Application Security
- Vulnerability Assessments
TRAINING SERVICES
- Information Security Fundamentals
- Risk Assessment Methodologies and Tools
Digital Forensics Methodologies and Tools
- Web Application Security
- GDPR Compliance Methodology
- IT Audit
STORM.
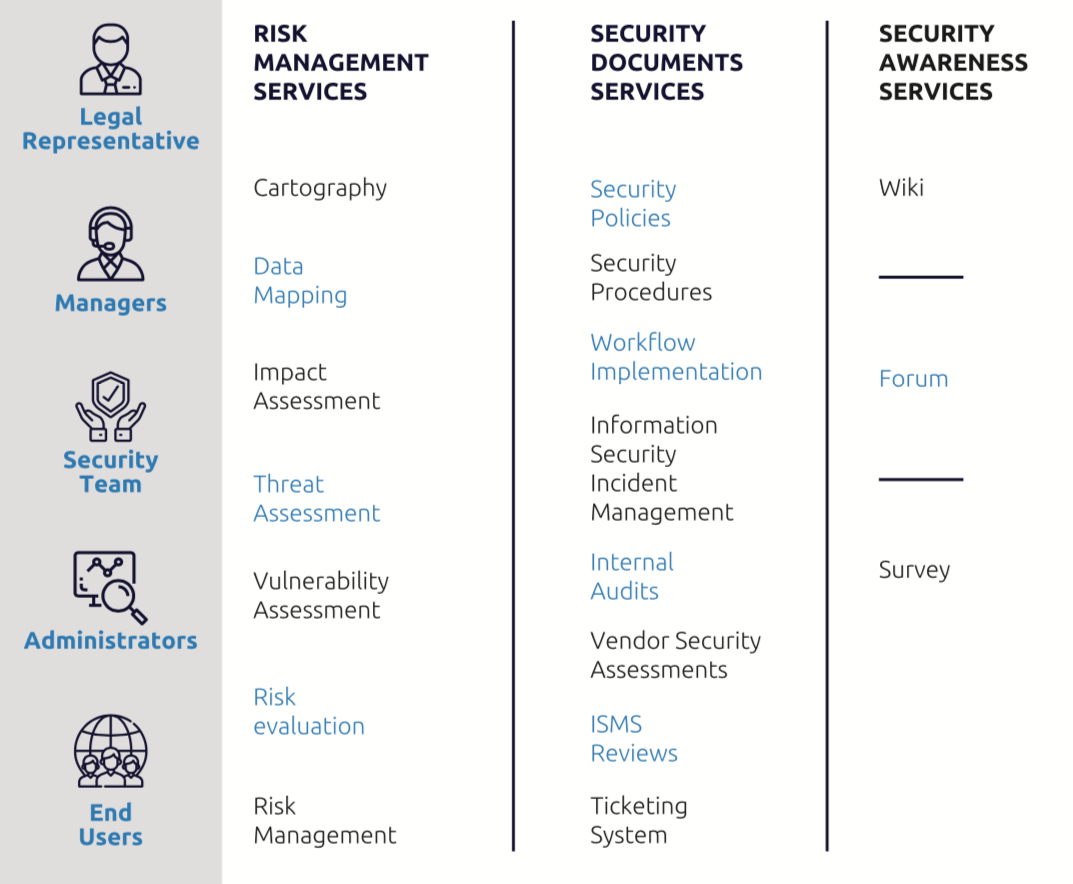
STORM is an innovative, collaborative, cost effective and user-friendly security consultancy environment that can be used by different type of organisations in order to collaboratively manage their information security.
STORM can easily be parameterised in order to address the needs of different types of Information and Communication Technology (ICT) systems (i.e. critical infrastructures, SMEs).
STORM environment offers a bundle of targeted services to the ICT users in order to guide them to securely manage their ICT systems, according the security best practices (NIST, SANS), standards (i.e. ISO 27001, ISO 27002, ISO 27005) and regulations (i.e. GDPR).
STORM: A unified platform designed for compliance with industry specific cybersecurity requirements (e.g. ISO 27001:2022, GDPR, IMO, NERC CIP etc.)

IS IN OUR DNA.